July, 2016 - Information & Security Notices
This page offers general news on the changing development in the evolving world of technology, as well as valuable security advice. I've also added tidbits and news items from around the world of technology. Hope you enjoy them.

Tech News
Wi-Fi Different From Wireless
There is a bit of confusion, even from people who know a lot about technology, in the terms Wi-Fi and wireless. They are often used interchangeably, but they are really two different terms. In fact, in the past, I was guilty myself of misusing the terms.
First, wireless means, literally, without wires. That encompasses a lot, including your wireless keyboard and mouse, Bluetooth connections, but also your Internet connection. It’s really a general term and can, in certain situations, have nothing to do with the Internet. For example, when you plug in the USB receiver for your wireless keyboard, you don’t need an Internet connection to use the keyboard, it communicates wirelessly, through that receiver.

Wireless also has been used to refer to broadband Internet connections, such as you would use on your Smartphone or tablet. Wireless is a much more broad term than Wi-Fi.
Wi-Fi, refers to the standard you use to connect to the Internet. Wi-Fi is part of wireless, but is not the same thing. The term Wi-Fi indicates a specific communication standard to allow computers to share resources and files. You generally need a router or an access point to broadcast a Wi-Fi signal. To use Wi-Fi, the devices must be fairly close together because of the limited range of the signal.

One way to help understand that difference in wireless and Wi-Fi is to think of your Smart phone. When you’re using it in your home or business, you more than likely are connected to the Wi-Fi network. You’ll see the Wi-Fi icon to indicate you are connected. (By the way, I just discovered that the up and down arrows mean uploading and downloading, as a little bonus tip!)

However, if you get further away from any access points while using your phone, you will switch over to the wireless, or broadband/cellular network. This is usually indicated by the strength bars or a 3G/4G/LTE indicator.

So while you may have thought they were the same thing, wireless and Wi-Fi are really two different terms, but mean similar things. Just remember that Wi-Fi is specific to connecting to the Internet, whereas wireless is a more general term for using anything without wires.

Windows Privacy
Microsoft Comes Clean About Windows Privacy
But the company decided to clear the air with a long, detailed blog post about their privacy policies for Windows 10. The post was long and detailed, but the company did list two simplified rules that it says governs the way they control privacy.
1. Windows 10 collects information so the product will work better for you.
2. You are in control with the ability to determine what information is collected. The company says there are three layers of data collected.1. Safety and Reliability – the company collects data about crashes and other system issues. The data includes an anonymous device ID and app crash data. They promise they don’t include your contents or files or anything that could possibly identify you.
Microsoft cites as an example some problems with a graphics driver that was crashing on Windows 10 PCs. Because of the crash reports, they contacted the developer of the driver and were able to come up with fix that they were able to test out on members of the Windows Insider program and then distribute to users at large within 48 hours of becoming aware of the issue.
2. Personalization – this information allows Microsoft to do things like have Cortana show you the scores for your favorite teams or offer up news stories for topics you’re interested in.
Users have complete control over this information and can update their settings to turn these functions off.
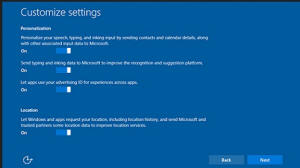
3. The data they don’t collect. Microsoft does not scan the contents of your email, communications or other files to deliver targeted advertising content. Other mail providers do this, and they think it makes them stand out.
If you enable Cortanta, you can give your digital assistant permission to look for things like shipping notices and flight delays in your e-mail, so you can be alerted. But that’s entirely up to you and that information would be for you on your device and not for Microsoft’s consumption.
If you’d like to check out the updated privacy policy for Windows services, click here.

Warn People About This Scam
A concerned reader named Terry wants to make sure everyone knows about this scam. She writes:
BIG QUESTION: Have received suspicious email messages like this many times and NEVER open them. They begin Hello Terry – then a link and then the first name of someone I know. I forwarded it to her, told her NOT to open the link and asked if this was from her. Her answer is below. You might want to warn your subscribers about this VERY PERVASIVE PROBLEM. Now the question – who can I report this to so the perp can be caught???????
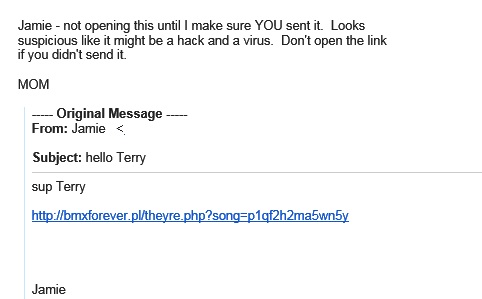
And here’s her daughter’s response.
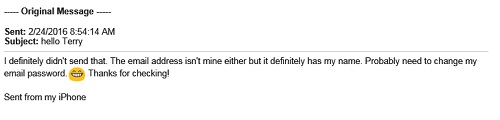
The good news is that you did exactly the right thing. Never click on a strange link without checking. E-mails like this are far too common. We get several of them a day to our customer service address.
The issue with reporting them to the police is that they are almost always generated from overseas. U.S. law enforcement has no authority there and for many countries, running spam e-mail operations is a big business.
Your best bet is to keep marking e-mails like this as Spam. It helps teach your e-mail account to filter these types of messages out.
This e-mail may or may not have actually come from your daughter’s e-mail account. She can check the sent messages folder to find out, but it’s likely her e-mail address was simply spoofed and used to make you think that’s where the e-mail was coming from.
Someone may have acquired her contact list because either your PC or mobile device or her PC or phone was compromised. But it’s also possible that the contact list of a person who has both of you in their contacts was compromised.
Still, she’s smart to change her password. Both of you should also make sure you have up-to-date anti-virus and malware software in place. You can report scams like this to the Federal Trade Commission by forwarding the message to spam@uce.gov and also to phishing.org/report-phishing. The Anti-Phishing Working Group — which includes ISPs, security vendors, financial institutions and law enforcement agencies — uses these reports to fight phishing.

